Сценарии использования
С помощью VAS сотрудники отделов расследований изучают страховые операции, находят признаки страхового мошенничества, определяют отношения между страховой компанией и ее клиентами, служащими и сторонними организациями.
Мошенничество со страховкой и инсценировка ДТП — один из наиболее частых кейсов мошенничества в страховой сфере. Расследовать такие случаи непросто, и многое зависит от профессионализма сотрудников страховой. VAS помогает ускорить расследования, визуализировать неочевидные связи между фигурантами и вскрывать факты, которые сложно обнаружить без аналитического инструмента.
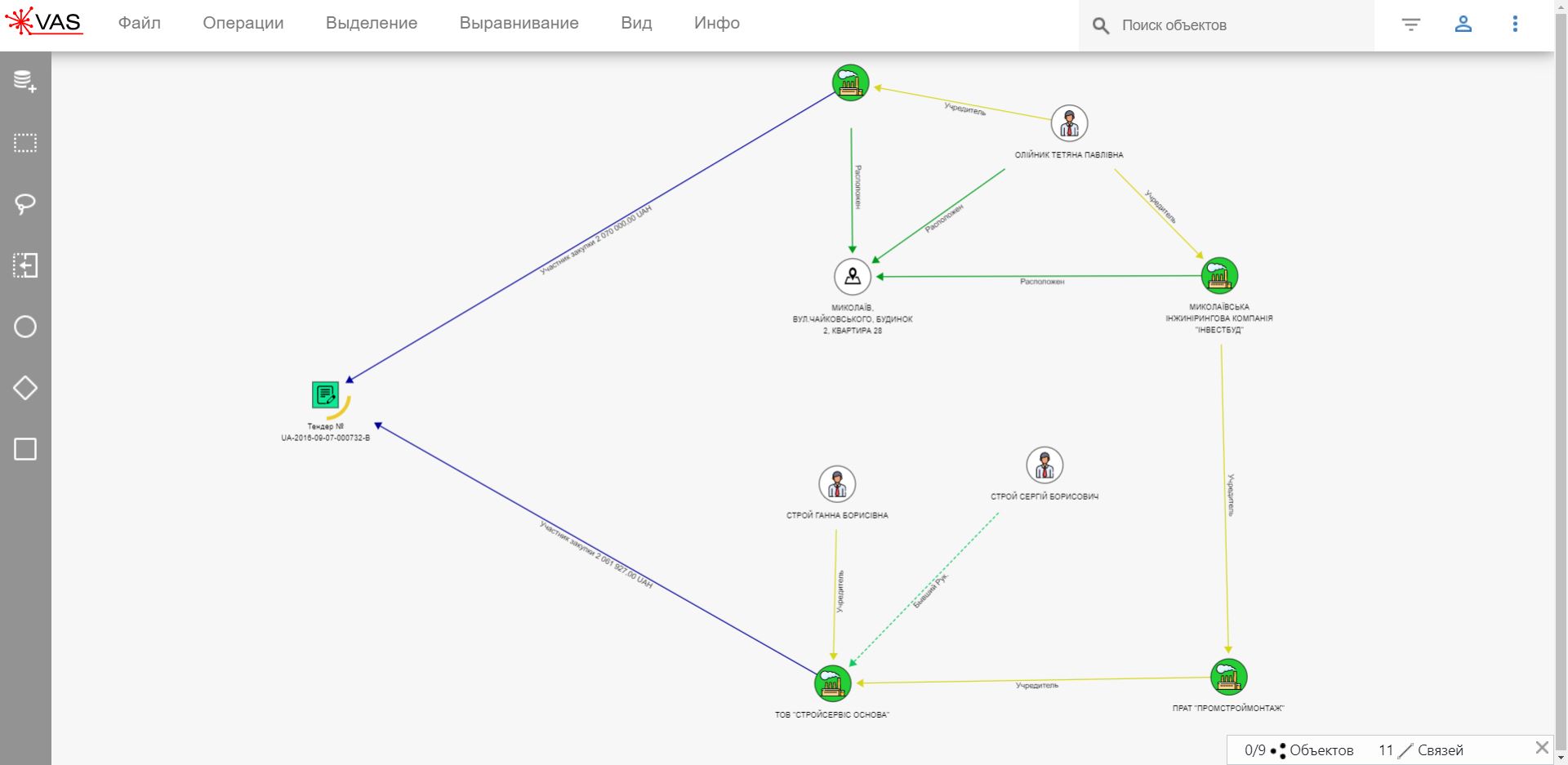
Мошенничество при закупках.
Обнаружение аффилированных компаний
При проведении тендеров сотрудники предприятий анализируют участников. Рассматривают претендентов по отдельности и часто не обнаруживают ничего подозрительного.
При анализе этих же данных с помощь VAS можно проверить, не связаны ли учредители подаваемых предприятий организационно учредительными связями через еще одну компанию. Это помогает выявлять риски увеличения стоимости работ до проведения аукциона и заключения договора.
Расследование экономических преступлений
При организации коррупционных схем должностные лица ведут себя осторожно, тщательно маскируя преступления. Например, регистрируя компании-однодневки на друзей. В такой схеме далеко не всегда можно установить связи между людьми. В рамках уголовного дела правоохранители получают доступ к информации о совместных выездах за границу, телефонных разговорах, предыдущих местах работы и прочее. Вручную проанализировать такой массив данных сложно, поэтому и нужен инструмент аналитики VAS.
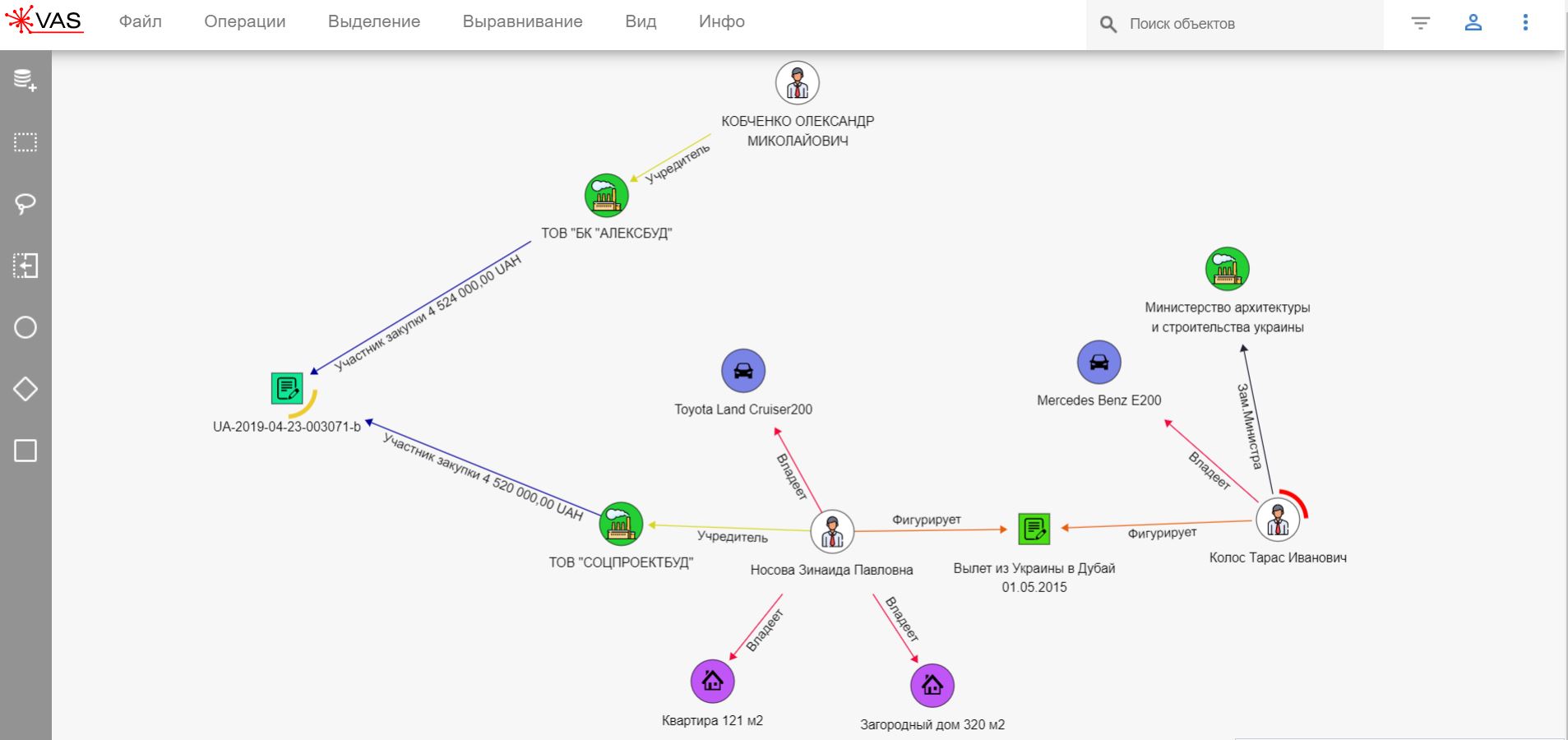
Выявление схемы уклонения от уплаты налогов.
Вывод денежных средств через ИП
Продукт визуализирует поступившие денежные средства от заинтересованных юридических лиц, которые переводят их на счета подконтрольных ИП с целью ухода от уплаты налогов и получения наличных денежных средств. Служба безопасности может легко зафиксировать мошенническую схему.
Киберугрозы.
Распределенная атака на инфраструктуру компании
SIEM-система фиксирует инцидент, например, попытку подбора пароля, сканирование сети, DDoS-атаку. В данном кейсе VAS интегрирован с IBM QRadar. Данные отображаются в VAS в виде единой наглядной схемы атаки: видны IP-адреса, можно вычислить и физические локации, с которых ведется атака.